December 23rd, 2025
Improved
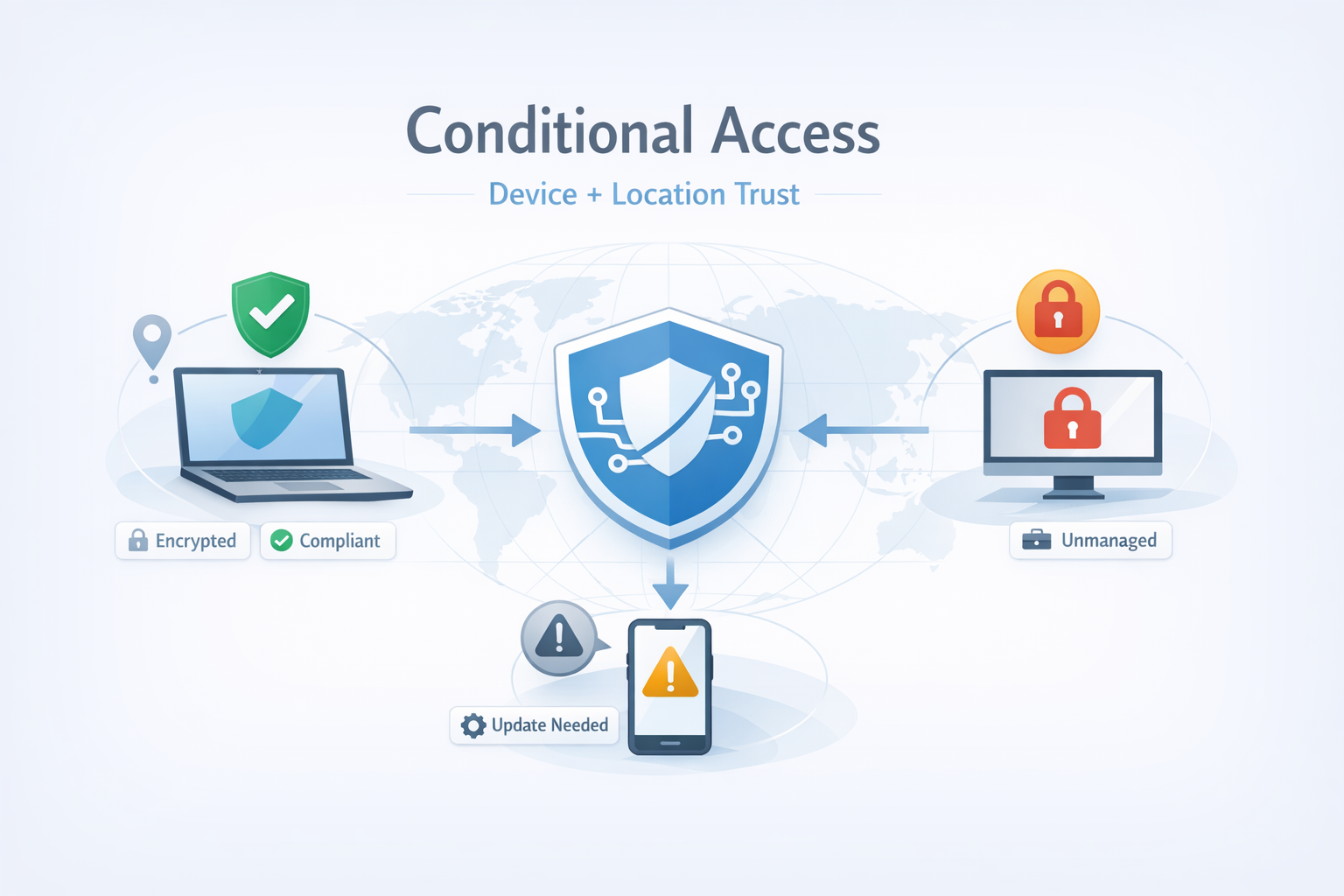
Conditional Access with Geolocation Trust and Device-Based Access ⭐
Trio’s Conditional Access module introduces policy-driven, context-aware access control that evaluates both device posture and real-time location trust before allowing authentication or session continuation. This enables Zero Trust decisions that are not static or identity-only, but continuously validated against device and environmental context.
What’s New
Conditional Access in Trio adds a dedicated enforcement layer where access is granted only when a request satisfies multiple signals, including:
Device-based access: whether the requesting endpoint is enrolled, trusted, and compliant
Geolocation trust: whether the request originates from an approved geographic context, as defined by policy
This module enables “allow/deny/step-up” behavior at the moment of access—based on the device’s current state and the user’s location context.
How It Works (Technical Overview)
When a user or device attempts to access a protected resource, Trio evaluates an access policy using a set of conditional inputs:
1) Device posture evaluation
Enrollment status (managed vs unmanaged)
Compliance state against assigned policies (e.g., encryption enabled, screen lock, OS requirements)
Device trust state (e.g., approved device identity, risk posture derived from agent telemetry where applicable)
2) Real-time location evaluation
Location is assessed against policy-defined trust criteria (e.g., permitted regions, office locations, or geofenced zones)
If location trust is required, access is allowed only if the device location matches the expected context at request time
3) Decision and enforcement
Trio returns an access decision:
Allow if all conditions pass
Deny if any mandatory condition fails
Conditional/step-up (where supported) if policy requires additional verification when risk is elevated (e.g., location mismatch or partial compliance)
Critically, this model supports dynamic enforcement: if device compliance changes or location context shifts, access can be re-evaluated based on policy.
Why It Matters
Identity-based access alone cannot prevent access from:
A valid user signing in from an unmanaged device
A trusted device operating outside approved geographic context
A device that was compliant yesterday but is non-compliant now
Conditional Access addresses these gaps by enforcing contextual authorization at runtime. The result is stronger resistance to credential theft, unauthorized access, and policy drift.
Platform Impact
Acts as a primary enforcement layer for Zero Trust access decisions
Integrates with IdP, Device SSO, and Device Login by adding context-based gating
Improves auditability by linking access outcomes to:
device identity
device compliance state
location context at time of request
Reduces manual incident response by preventing risky access paths by default
Who Should Use This
Organizations implementing Zero Trust across distributed teams
IT/security teams that need to restrict access by trusted device + trusted location
Environments with sensitive data requiring deterministic access controls and audit trails
Teams that need policy-driven enforcement rather than manual approvals